Network Security Threats Prevention
Network Security Threats Prevention
Encryption Method
The universal technique for providing confidentiality for transmitted data is symmetric encryption. A symmetric encryption scheme has five components.
a. Plaintext : This is the original message or data that is fed into the algorithm as input.
b. Encryption algorithm : The encryption algorithm performs various substitutions and transformations on the plaintext.
c. Secret key : The secret key is also input to the encryption algorithm. The exact substitutions and transformations performed by the algorithm depend on the key.
d. Ciphertext : This is the scrambled message produced as output. It depends on the plaintext and the secret key. For a given message, two different keys will produce two different ciphertexts.
e. Decryption algorithm : This is essentially the encryption algorithm run in reverse. It takes the ciphertext and the secret key and produces the original plaintext.
Cryptographic Algorithms
There are several ways of classifying cryptographic algorithms. For purposes of this paper, they will be categorized based on the number of keys that are employed for encryption and decryption, and further defined by their application and use. The three types of algorithms that will be :
» Secret Key Cryptography (SKC) : Uses a single key for both encryption and decryption,
» Public Key Cryptography (PKC) : Uses one key for encryption and another for decryption.
» Hash Functions : Uses a mathematical transformation to irreversibly "encrypt" information.
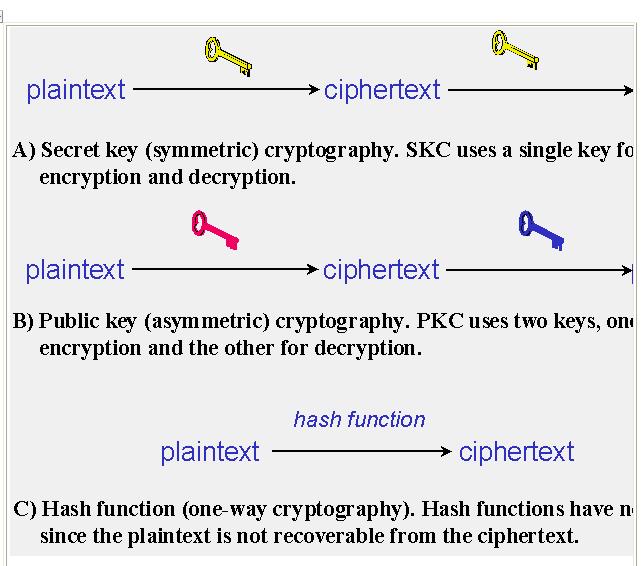
Cryptographic Algorithms
Secret Key Cryptography
With secret key cryptography, a single key is used for both encryption and decryption. As shown in Figure 33A, the sender uses the key (or some set of rules) to encrypt the plaintext and sends the ciphertext to the receiver. The receiver applies the same key (or ruleset) to decrypt the message and recover the plaintext. Because a single key is used for both functions, secret key cryptography is also called symmetric encryption.
With this form of cryptography, it is obvious that the key must be known to both the sender and the receiver; that, in fact, is the secret. The biggest difficulty with this approach, of course, is the distribution of the key.
Secret key cryptography schemes are generally categorized as being either stream ciphers or block ciphers. Stream ciphers operate on a single bit (byte or computer word) at a time and implement some form of feedback mechanism so that the key is constantly changing. A block cipher is so-called because the scheme encrypts one block of data at a time using the same key on each block. In general, the same plaintext block will always encrypt to the same ciphertext when using the same key in a block cipher whereas the same plaintext will encrypt to different ciphertext in a stream cipher.
Stream ciphers come in several flavors but two are worth mentioning here. Self-synchronizing stream ciphers calculate each bit in the keystream as a function of the previous n bits in the keystream. It is termed "self-synchronizing" because the decryption process can stay synchronized with the encryption process merely by knowing how far into the n-bit keystream it is. One problem is error propagation; a garbled bit in transmission will result in n garbled bits at the receiving side. Synchronous stream ciphers generate the keystream in a fashion independent of the message stream but by using the same keystream generation function at sender and receiver. While stream ciphers do not propagate transmission errors, they are, by their nature, periodic so that the keystream will eventually repeat.
Block ciphers can operate in one of several modes; the following four are the most important:
» Electronic Codebook (ECB) : This mode is the simplest, most obvious application: the secret key is used to encrypt the plaintext block to form a ciphertext block. Two identical plaintext blocks, then, will always generate the same ciphertext block. Although this is the most common mode of block ciphers, it is susceptible to a variety of brute-force attacks.
» Cipher Block Chaining (CBC) : This mode adds a feedback mechanism to the encryption scheme. In CBC, the plaintext is exclusively-ORed (XORed) with the previous ciphertext block prior to encryption. In this mode, two identical blocks of plaintext never encrypt to the same ciphertext.
» Cipher Feedback (CFB) : This mode is a block cipher implementation as a self-synchronizing stream cipher. CFB mode allows data to be encrypted in units smaller than the block size, which might be useful in some applications such as encrypting interactive terminal input. If we were using 1-byte CFB mode, for example, each incoming character is placed into a shift register the same size as the block, encrypted, and the block transmitted. At the receiving side, the ciphertext is decrypted and the extra bits in the block (i.e., everything above and beyond the one byte) are discarded.
» Output Feedback (OFB) : This mode is a block cipher implementation conceptually similar to a synchronous stream cipher. OFB prevents the same plaintext block from generating the same ciphertext block by using an internal feedback mechanism that is independent of both the plaintext and ciphertext bitstreams.
Public-Key Cryptography
PKC depends upon the existence of so-called one-way functions, or mathematical functions that are easy to computer whereas their inverse function is relatively difficult to compute. In PKC, one of the keys is designated the public key and may be advertised as widely as the owner wants. The other key is designated the private key and is never revealed to another party. It is straight forward to send messages under this scheme. Suppose Shams wants to send Aadil a message. Shams encrypts some information using Aadil‟s ublic key; Aadil decrypts the ciphertext using his private key. This method could be also used to prove who sent a message; Shams, for example, could encrypt some plaintext with his private key; when Aadil decrypts using Shams‟s public key, he knows that Shams sent the message and Shams cannot deny having sent the message (non-repudiation).
Hash Functions
Hash functions, also called message digests and one-way encryption, and are algorithms that, in some sense, use no key Instead, a fixed-length hash value is computed based upon the plaintext that makes it impossible for either the contents or length of the plaintext to be recovered. Hash algorithms are typically used to provide a digital fingerprint of a file's contents often used to ensure that the file has not been altered by an intruder or virus. Hash functions are also commonly employed by many operating systems to encrypt passwords. Hash functions, then, provide a measure of the integrity of a file.
